Accellion Data Breach Involving Sensitive Information Impacts Multiple Entities
Home Help Center Accellion Data Breach Involving Sensitive Information Impacts Multiple Entities
- IT security provider Accellion suffered an attack on their file-sharing product. It resulted in multiple entities being impacted by the Accellion data breach, including the Office of the Washington State Auditor.
- A data breach at Astoria Company, LLC. led to a database with 300 million user’s data being offered for sale by cybercriminals. According to Night Lion Security, the database is believed to have 20 million users’ Social Security numbers (SSNs) and bank account information, and 30 million users ’ sensitive medical data.
- The California Department of Motor Vehicles suffered a security incident after third-party, Automatic Funds Transfer Services, Inc., was the victim of a ransomware attack in early February. The attack may have compromised 38 million records of millions of Californians over the last 20 months.
- For more information about February data breaches, consumers and businesses should visit the Identity Theft Resource Center’s (ITRC) data breach tracking tool, notified.
- If you believe you are a victim of identity theft from a data breach, contact the ITRC toll-free at 888.400.5530 or through live-chat on the company website.
Notable February Data Breaches in 2021
Of all the data breaches the Identity Theft Resource Center (ITRC) tracked in February, three stood out: Accellion, Astoria Company, LLC. and the California Department of Motor Vehicles. All three data events are notable for unique reasons. One event happened when a file-sharing product was targeted in a highly sophisticated cyberattack that affected many well-known entities; another event, which occurred after an attack by ShinyHunters, led to a 300 million user database being offered for sale – a database that includes an array of sensitive personally identifiable information (PII); the third event may have compromised as many as 38 million driving records.
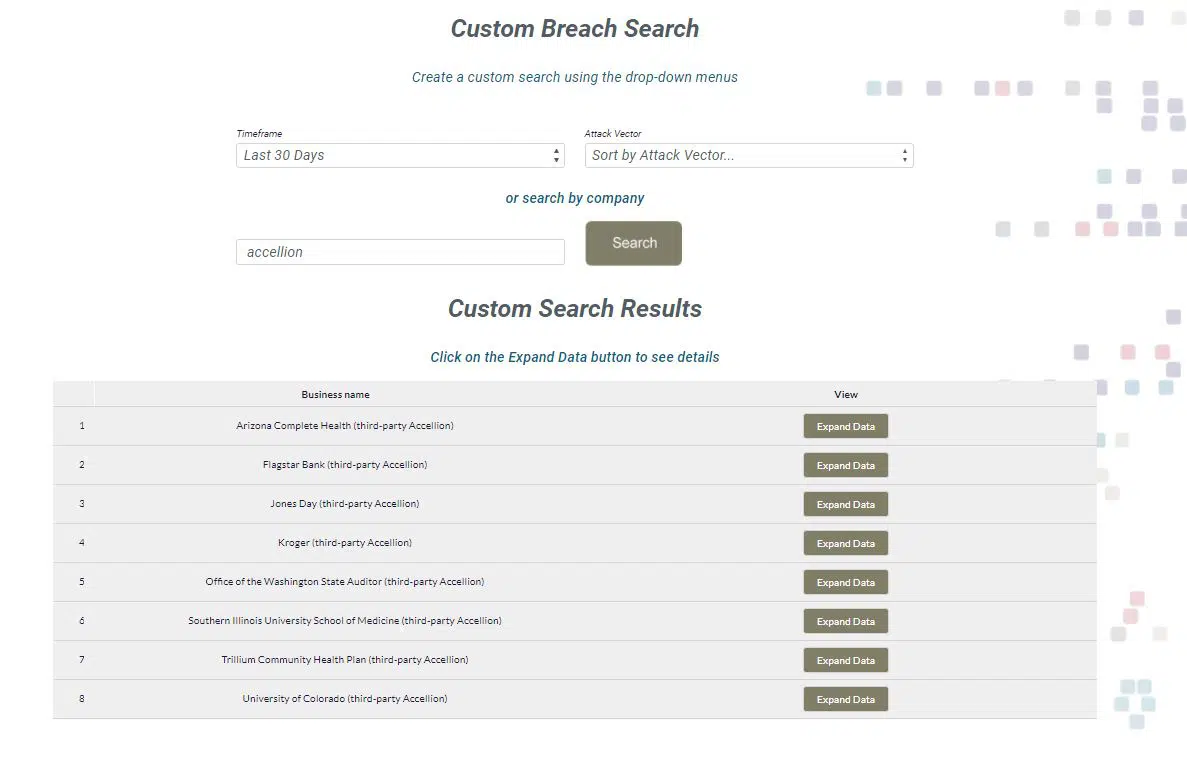
Accellion
IT security provider, Accellion, was the target of an attack, first disclosed in late December, that targeted Accellion’s 20-year-old file-sharing product, File Transfer Appliance (FTA). According to TechTarget, the attackers utilized a zero-day vulnerability in FTA in what Accellion called a “highly sophisticated cyberattack.” Threat actor motivations were not immediately clear. However, FireEye recently published research that showed the Accellion data breach was the work of threat actors the vendor identified as UNC2546, which have connections to Clop ransomware.
The Accellion data breach has impacted multiple entities in the U.S. They include Flagstar Bank, Jones Day, Qualys, Kroger, University of Colorado and, most notably, the Office of the Washington State Auditor. The breach may have also impacted Goodwin Law, Southern Illinois University School of Medicine, Trillium Community Health Plan and Harvard Business School.
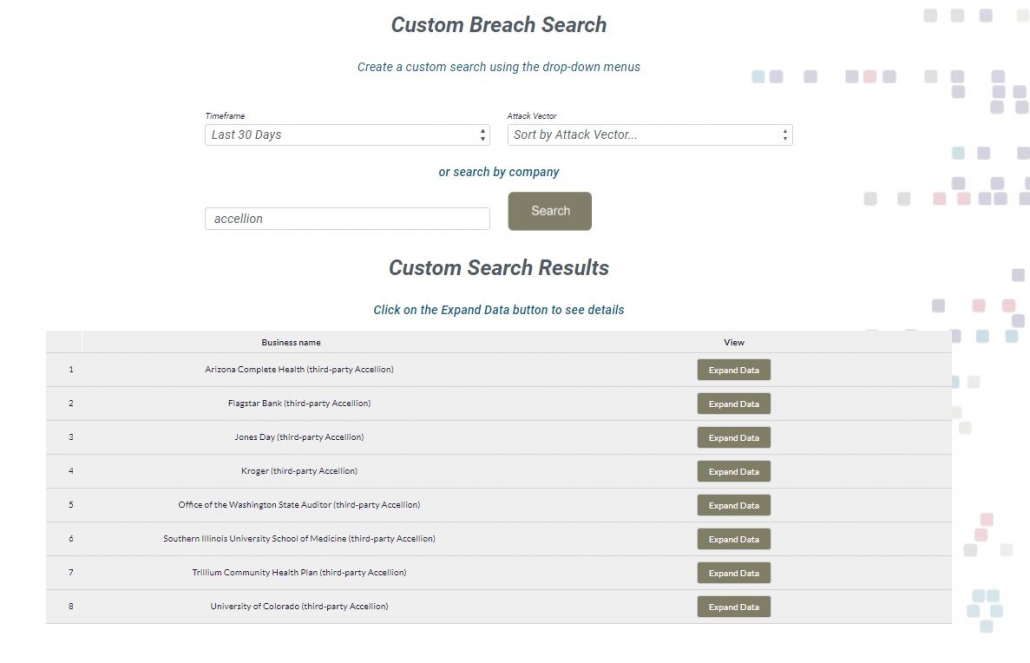
The information exposed varies by entity. However, a notice from the Office of the Washington State Auditor says the data includes personal information from about 1.6 million unemployment claims made in 2020 to the office, as well as other information from some state agencies and local governments.
Astoria Company, LLC.
Marketing company Astoria Company, LLC. fell victim to an attack by the ShinyHunters cybercrime group. According to Night Lion Security, the threat intelligence team became aware of several new large data breaches being sold by ShinyHunters, including a 300 million user database from Astoria.
The Astoria database is believed to have 40 million users’ Social Security numbers (SSNs), 20 million users’ SSNs and bank account information, and 30 million identities linked to sensitive medical data. Night Lion Security says every lead within the database contained, at a minimum, names, email addresses, dates of birth, mobile phone numbers, physical address and IP addresses.
California Department of Motor Vehicles
The California Department of Motor Vehicles (DMV) is investigating a security breach that may have compromised as many as 38 million records of millions of Californians over the last 20 months. According to Patch, a company the California DMV contracts with to verify vehicle registration addresses – Automatic Funds Transfer Services, Inc. – was the victim of a ransomware attack in early February. Automatic Funds Transfer Services, Inc. has access to the names, addresses, license plate numbers and vehicle identification numbers of registrants. However, the DMV says it does not have access to SSNs, birthdates, voter registration information, immigration status or driver’s license information.
In a recent press release, the DMV said its systems have not been compromised, and it is unknown if DMV data shared with Automatic Funds Transfer Services, Inc. has been compromised. The DMV immediately stopped all data transfers to the company and notified law enforcement, including the Federal Bureau of Investigation (FBI).
What to Do if These Breaches Impact You
Anyone who receives a data breach notification letter should follow the advice offered by the company. The ITRC recommends immediately changing your password by switching to a 12+-character passphrase, changing the passwords of other accounts with the same password as the breached account, considering using a password manager, and keeping an eye out for phishing attempts claiming to be from the breached company.
The California DMV asks anyone who spots suspicious activity on their account to report it to law enforcement.
The Office of the Washington State Auditor has set up a website for the latest information on the Accellion data breach and its impacts on the State Auditor’s Office.
notified
For more information about February data breaches, or other data breaches, consumers and businesses should visit the ITRC’s data breach tracking tool, notified, free to consumers.
Organizations that need comprehensive breach information for business planning or due diligence can access as many as 90 data points through one of the three paid notified subscriptions. Subscriptions help ensure the ITRC’s identity crime services stay free.
Contact the ITRC
If you believe you are the victim of an identity crime or your identity has been compromised in a data breach, you can speak with an ITRC expert advisor at no-cost by phone (888.400.5530) or live-chat. Just go to www.idtheftcer.org to get started.
How much information are you putting out there? It’s probably too much. To help you stop sharing Too Much Information, sign up for the In the Loop.
Get ID Theft News
Stay informed with alerts, newsletters, and notifications from the Identity Theft Resource Center

